
MOBILE APPS AND BUSINESS
January 8, 2022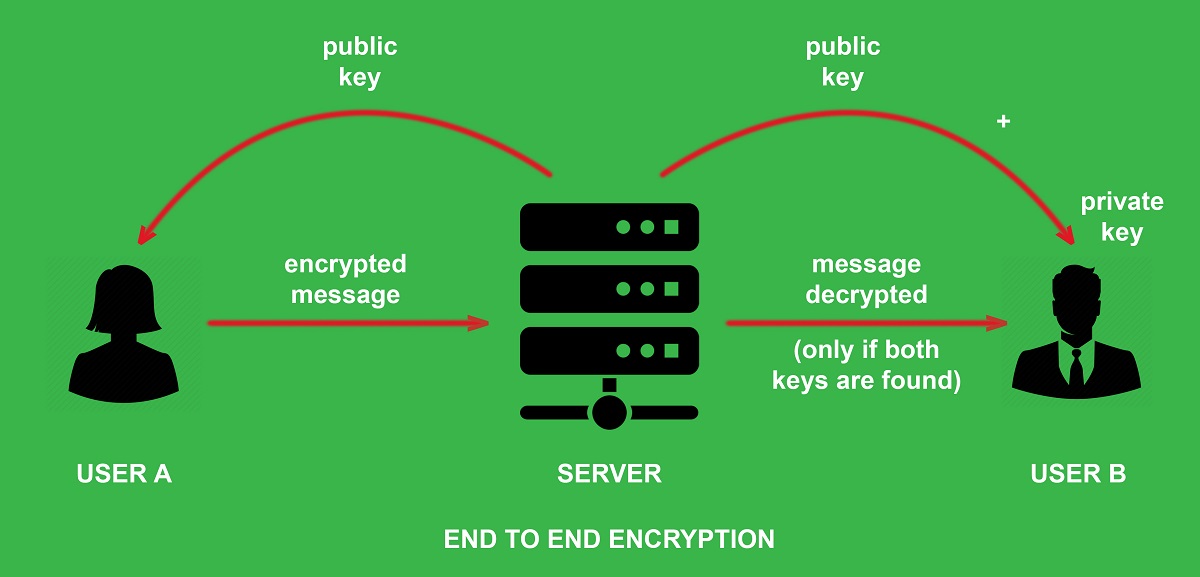
End to End Encryption
February 2, 2022You’ve probably gotten used to my simple blog posts for regular followers of this blog. Today, I have decided to touch on the more technical stuff. I will simplify data masking to the best of my ability.
What is Data Masking?
Data masking is the process of modifying sensitive data to be of no or little value to unauthorized intruders while still being usable by software or authorized personnel. It is a data-security practice that uses encryption, tokenization, and data obfuscation to create data that appears different from data that an individual did not mask. In data masking, masked data replaces the original data. The masked data contains similar characteristics but cannot compromise security. Some experts use the terms data masking and data obfuscation interchangeably.
History
Data masking started in the 1990s as a data security best practice that evolved from data encryption. The data security industry adopted it as a data security solution because it does not require application and database code changes. One can implement it at the data layer without affecting existing applications or databases. A data layer is a layer of your website that contains all of the data generated by visitors engaging with your website. Companies like Microsoft, IBM, Verizon, Telefónica, JP Morgan, Wells Fargo, and Deloitte currently use it. This is mainly because of the data security benefits it offers.
Types of data masking methods
Companies use three main methods to secure data: data redaction, encryption, and tokenization.
Data Redaction is the removal or replacement of data that is considered sensitive data with one or more non-sensitive data points. Data redaction has been around since the beginning of data masking. Today it remains one of the most frequently used methods.
Data Encryption is the process through which data is protected by an encryption algorithm so that it can only be decrypted and read by someone who has access to a decryption key. It is an effective data security solution that organizations have adopted over the years.
Tokenization is the process of replacing sensitive data with unique identification symbols so that data can be reused or re-encrypted without being exposed to any vulnerabilities. It was developed in the credit card industry as a data security best practice to reduce fraud associated with data breaches. Tokenization is different from data encryption in that data encryption replaces sensitive data with random symbols.
In contrast, tokenization replaces data with symbols that map back to the data they represent. This masking technique replaces data with non-sensitive data points referred to as tokens. Tokens are used instead of sensitive data throughout the data life cycle, including during data input, output, storage, and sharing. Tokenization enhances data security because it does not require data re-write or changing the data format. Today companies have adopted data tokenization as a data security solution because it allows companies to break data into smaller chunks and then reassemble the data when needed.
Experts in the field consider tokenization the most secure method because unauthorized personnel can’t reconstruct data.
Development of data masking
The data security industry adopted data masking as a data security solution because it does not require application and database code changes. As a result, data masking vendors adopted this data security solution, becoming a data security best practice. As data breaches increased, so did the demand for data security solutions.
It has become a robust data security solution for companies that collect, store, or process sensitive data about individuals to help ensure compliance with data privacy laws and data security regulations.
Developers initially intended data masking to secure data through data redaction techniques, which replace certain data elements with NULLs or replace them with a note about data replacement.
Today’s data masking technologies not only protect data from theft but also help organizations comply with data privacy mandates. These mandates include data-breach reporting, data subject data requests and data location requirements.
Data masking is widely used worldwide in data centres and cloud environments such as Amazon Web Services (AWS), Microsoft Azure, IBM Cloud, VMware Cloud on AWS, and many others. The data security benefits it offers has made it a data security best practice. Data protection authorities such as the National Institute of Standards and Technology (NIST) (U.S.A) and data privacy regulators such as the European Union (EU) recommend it.
Trends
Global governing bodies have increased focus on data privacy. These bodies include the European Union’s General Data Protection Regulation (GDPR) and Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA). As a result, data masking has evolved into data security and privacy best practice that enables data protection even after data has left the data centre.
In addition, companies use data masking across all data types, including Big Data, document data, structured data and unstructured data.
Organizations use data masking to support data governance, security, and privacy initiatives. Data redaction has become the de facto data protection process for data at rest. Data encryption has also emerged as an alternative approach.
Advantages
Data masking can help ensure organizations meet their data compliance obligations. It protects companies against unauthorized data access and data loss. Furthermore, it allows companies to remain secure even after data has left the centre. It achieves this by enabling sharing externally without relinquishing control of sensitive data.
In addition, it can help prevent data breaches, helping organizations keep their data safe from attacks.
Disadvantages
Data masking cannot address all data security risks. First, it does not prevent data breaches when data is in motion. It also doesn’t address data security issues associated with information already breached. Examples of information breaches are data leakage and data exfiltration.
While data masking can protect against unauthorized access to data, this protection does not extend to information in motion.
Why organizations should adopt data masking
Data masking is data obfuscation that modifies data to make data unrecognizable to hackers without stopping data from working. It must be part of any data security strategy. This is because it protects against unauthorized access. In addition, it also safeguards data when it leaves the data centre. Finally, it helps organizations to remain data compliant.
At Softlink Options, we work with all organizations invested in big data that require data security solutions. Check out our data backup and security packages. CONTACT US in case of any queries. We take pride in the quality of our products and services.



